Assignment 4
DEVELOPING INTIMACY WITH YOUR DATA
This exercise involves you working with a dataset of your choosing. Visit the website, browse through the options and find a dataset of interest, then follow the simple instructions to download it. With acquisition completed, work through the remaining key steps of examining, transforming and exploring your data to develop a robust familiarisation with its potential offering:
Examination: Thoroughly examine the physical properties (type, size, condition) of your dataset, noting down useful observations or descriptions where relevant.
Transformation: What could you do/would you need to do to clean or modify the existing data to create new values to work with? What other data could you imagine would be valuable to consolidate the existing data?
Exploration: Using a tool of your choice (such as Excel, Tableau, R) to visually explore the dat
- Information Systems
- February 4th, 2020
Pass A Value To A Function That Makes A Decision
Instructions
You will write a flowchart, and C code for a program that does the following:
- Within main(), it asks for the user's annual income.
- Within main(), it calls a function called printIt() and passes the income value to printIt().
- The printIt() function evaluates the income, and if the number is over 90000, prints a congratulatory message. If the income is not over 90000, it prints a message of encouragement, like "You WILL make $50,000, if you keep going."
Here is what the output looks like.
Submission Instructions
Upload your Flowgorithm file, your .c file, and a screenshot of your code output saved i
- Information Systems
- February 4th, 2020
Passing Variables By Address
Instructions
You may pass variables to functions either by address or by value. If you pass a variable by address, then both functions will see the changed value of the variable (if the value changes). If you pass a variable by value, you are really passing a copy of the variable, and the calling function will not see the changed value of the variable (if the called function changes its value).
Of note in this example:
You pass a variable by prepending the variable name with an ampersand (&).
The receiving function (in this case, do_fun()), prepends the variable name with an asterisk (*). This tells the receiving function that it's receiving the variable's address, not a copy of the variable.
Notice that the new value of the variable amt is visible in the do_fun() function and in main().
Here is the code:
- Information Systems
- February 4th, 2020
Passing User Values To A Function And Using The Return Value Of The Function
Instructions
This program gets values from the user, and then runs a calculation. The values are passed by reference (by address), so the main() function sees the changed values of the variables. The first function (getValues()) gets user input. The second function (calcCubic), performs the calculations, and the third function (printCubic()) prints the value of the calculation.
Here is the code:
And here is the output:
Submission Instructions
Now, you enter the code, and run it. (No flowchart this time)
Upload your .c file and a screenshot of your code output saved in a Word document
<- Information Systems
- February 4th, 2020
Write And Call Three Functions
Instructions
You will write a flowchart, and C code for a program that does the following:
Call three functions from main(). The functions are named first(), second(), and third(). Each function prints out its name ("first," "second," "third."). After all three functions are called, the main() function should print "End of program."
Here is what the program looks like.
Submission Instructions
Upload your Flowgorithm file, your .c file, and a screenshot of your code output saved in a Word document
- Information Systems
- February 4th, 2020
DB Project Modeling And Design
Assignment Details
You are working as a Quality Assurance Engineer. Your system integrates with several different systems. The following is an example of a high-level architecture diagram:
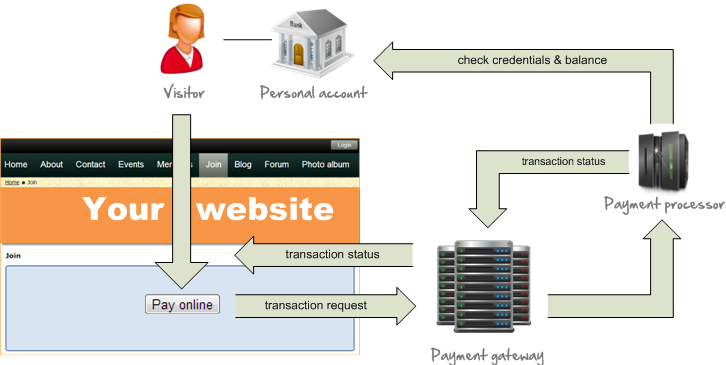
(Wild Apricot, n.d.)
Post the following for this discussion:
- Describe the challenges related to system integration testing in the above scenario.
- Provide at least 2 of the most important test cases that should be tested in the above architecture.
- Information Systems
- February 4th, 2020
Wk 1 – IT Governance
- Read the .
Imagine you are the IT manager for Gail Industries. You will meet with a new business analyst team at the Smallville customer site. The project sponsor has asked you to spend time with the business analyst team to emphasize the importance of IT governance.
Create a 10- to 12-slide media-rich overview and brief analysis presentation with speaker notes in which you:
- Examine the role of IT governance and why it is important in the IT industry.
- Analyze key aspects of IT governance, including enterprise resource planning and transaction processing systems.
- Please note that all assignments are required to have a minimum of 3 references with in-text citations. If you are unsure of what is required, please ask well in advance.
Media-rich: means that there are visuals and possibly audio files that enhanc
- Information Systems
- February 4th, 2020
Discussion-5(Tele)
Review the NIST Framework document at
Then, create a list of best practices for firewall and VPN man
Response#1 (Leburu)
Best Practices for Firewall Rules:
In a firewall rule, the action component decides if it will permit or block traffic. It has an action on match feature. For example, if the traffic matches the components of a rule, then it will be permitted to connect to the network. It is essential to consider the potential security risks when modifying a firewall rule to avoid future issues. (Agatsuma, S. (2020)
Types of Best Practices:
formal change procedure:
Firewall rules must be updated for new services and new devices. Before add or modify any firewall rules, each change that create requires that apply the change.
Block traffic by default:
By default, start blocking all traffic, only allo
- Information Systems
- February 4th, 2020
Examining Data Formats
Part 1: Multiple Formats
Download the four zipcodeDemographics files. These files contain the same data but in different formats. Using a text editor examine the files and note differences in their structure. Perform some research to obtain brief definitions of each format, write your definitions stating your referenced source(s). Is any format easier to read compared to the others? If so, why?
Examine the file and characterize it (i.e., pick a format to analyze). Imagine that you must present your findings to an executive committee that wants to know what is important in the data. Prepare a single PowerPoint slide to succinctly characterize the data.
Part 2: Data Wrangling
Data wrangling is the process of manipulating data to change it into a format that can be used for a
- Information Systems
- February 4th, 2020
Regular Expressions – Basic, UNIX, XML, And SQL
instructor's question for class discussion:
What is the importance of regular expressions in data analytics? Also, discuss the differences between the types of regular expressions. Choose two types of regular expressions and discuss the differences between the two. Please be sure to include two or three differences for each. Include how they help manipulate data.
Also, Reply to your classmates:
When replying to your classmate's posts, offer your opinion on what he/she thinks is the importance of regular expressions, whether you agree or disagree, and why.



